How to store encryption key in java images are ready. How to store encryption key in java are a topic that is being searched for and liked by netizens today. You can Find and Download the How to store encryption key in java files here. Download all royalty-free photos and vectors.
If you’re searching for how to store encryption key in java pictures information related to the how to store encryption key in java topic, you have pay a visit to the right blog. Our website always provides you with hints for refferencing the highest quality video and image content, please kindly surf and locate more enlightening video articles and graphics that match your interests.
How To Store Encryption Key In Java. As ArtjomB notes you would keep the key safe by not putting it into your program. 17012019 Additionally you can write some custom Java code to get the private key extracted as well. String key PasswordUtils. How to rotate a non-square image in Java.

 Customer Supplied Encryption Keys Documentation Google Cloud From cloud.google.com
Customer Supplied Encryption Keys Documentation Google Cloud From cloud.google.com
13082021 To implement input string encryption we first need to generate the secret key and IV according to the previous section. How to achieve method chaining in Java. Anything that doesnt look like that is no longer encryption or security its some form of obfuscation. This manages three different entries namely PrivateKeyEntry SecretKeyEntry TrustedCertificateEntry. The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store. How to draw path like canvas in Android using OpenGL ES 2.
The receiver inputs the decryption key into the decryption.
VerifyPassword Of Salesmen key salt 5. Are generic type parameters converted to Object for raw types. After all of the header information theres a long byte string. Below is the example class of EncryptDecryptjava. How to rotate a non-square image in Java. To save a symmetric key well need three things.

 Source: mkyong.com
Source: mkyong.com
08042021 Mostly the keys will stay unchanged for a long time. As the next step we create an instance from the Cipher class by using the getInstance method. The receiver inputs the decryption key into the decryption. Now you will see the console window for output. To begin with lets create a simple KeyStore.
 Source: documentation.commvault.com
Source: documentation.commvault.com
Run as a java application. To begin with lets create a simple KeyStore. After all of the header information theres a long byte string. The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store. How to rotate a non-square image in Java.
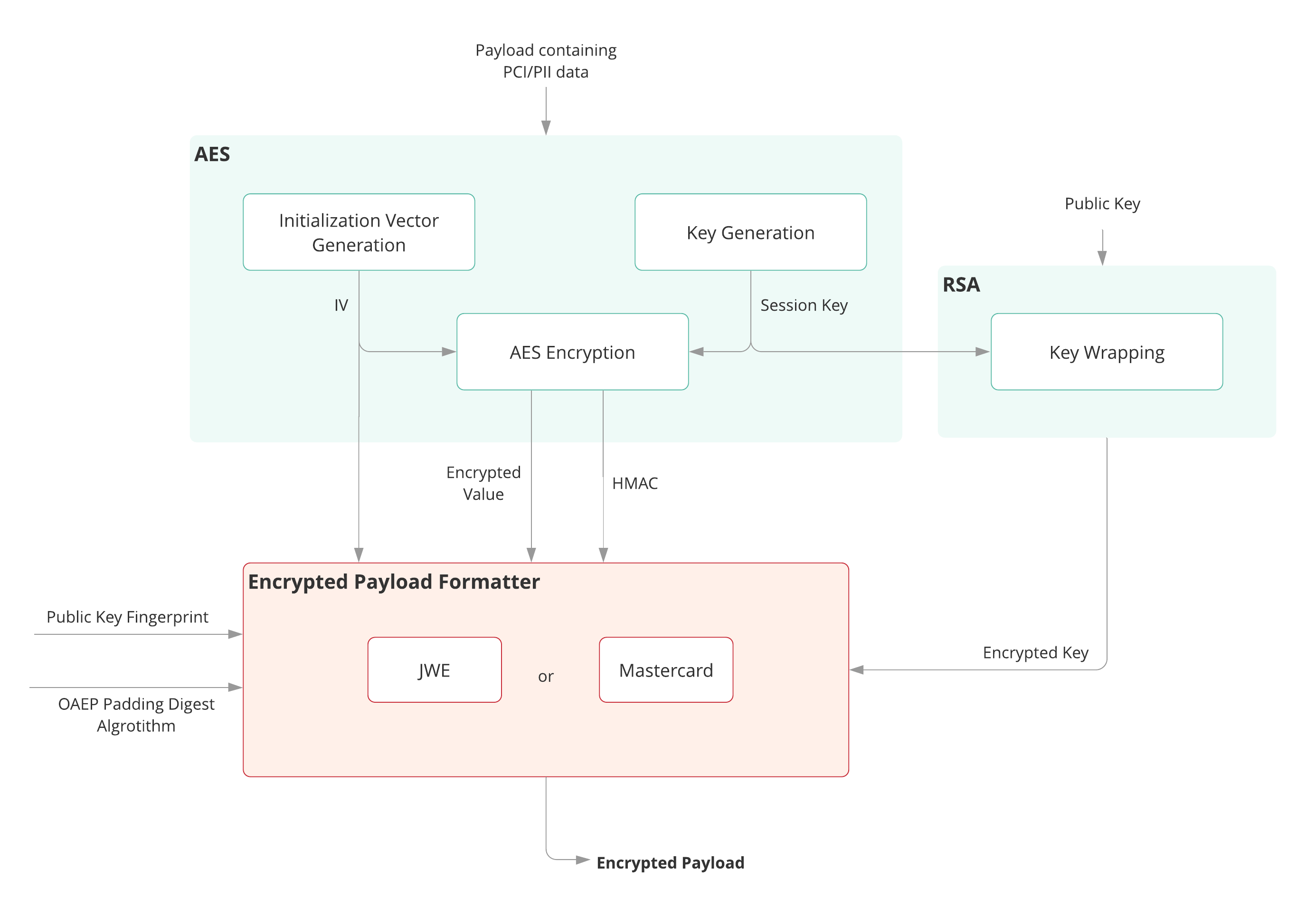 Source: developer.mastercard.com
Source: developer.mastercard.com
The apache commons codec Base64 methods were used to encodedecode string. 08042021 Mostly the keys will stay unchanged for a long time. I want to know how to securely store encryption key in Android. 08122011 You will then need to to find where to store the password for the keystore and and so on. The Keys and certificates usedgenerated are stored in a data base called as keystore.
 Source: pinterest.com
Source: pinterest.com
You may also specify the new password in the command by using the -new newpass option where newpass is the password. Depending on your security requirements and needs you could enrypt the data using symmetric encryption and retrieve the password via a remote server your server using client side certificate authentication. String key PasswordUtils. 04082021 Just press CtrlS to save or you can go to file and click on save. The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store.
 Source: pinterest.com
Source: pinterest.com
The keys were hard coded to prevent anyone to get the keys and use to decrypt string. An alias his is simply the name that well use in the future to refer to the entry a key which is wrapped in a KeyStoreSecretKeyEntry. Encryption Key is a value that is known to the sender. The apache commons codec Base64 methods were used to encodedecode string. How to rotate a non-square image in Java.
 Source: pinterest.com
Source: pinterest.com
Decryption Key is a value that is known to the receiver. Try FileOutputStream fos new FileOutputStreampublickey foswritepublicKeygetEncoded. Below is the example class of EncryptDecryptjava. Now you will see the console window for output. 1 keytool -genkeypair -alias notebook.
 Source: docs.mongodb.com
Source: docs.mongodb.com
During startup an authorized user or security device will need to provide the key. Decryption Key is a value that is known to the receiver. To begin with lets create a simple KeyStore. The sender inputs the encryption key into the encryption algorithm along with the plaintext in order to compute the cipher text. How to draw path like canvas in Android using OpenGL ES 2.
 Source: pinterest.com
Source: pinterest.com
The keys were hard coded to prevent anyone to get the keys and use to decrypt string. VerifyPassword Of Salesmen key salt 5. The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store. What is the best scenario to protect encryption and secrete keys. 04082021 Just press CtrlS to save or you can go to file and click on save.
 Source: fi.pinterest.com
Source: fi.pinterest.com
17012019 Additionally you can write some custom Java code to get the private key extracted as well. Java instantiate class from string. The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store. By default this database is stored in a file named keystore. 04082021 Just press CtrlS to save or you can go to file and click on save.
 Source: thesslstore.com
Source: thesslstore.com
The goal of this post is to develop some Java software that will apply the first few parameters to the last parameter and produce a decrypted private key which can then be imported into an existing Java Key Store. As ArtjomB notes you would keep the key safe by not putting it into your program. This is the encyrpted payload the private key itself. The apache commons codec Base64 methods were used to encodedecode string. 08122011 You will then need to to find where to store the password for the keystore and and so on.
 Source: cloud.google.com
Source: cloud.google.com
Keytool -storepasswd -keystore keystorejks. 04082021 Just press CtrlS to save or you can go to file and click on save. From your comments you need to encrypt data using a local key for current Android versions and the old ones Android Keystore is designed to generate and protect your. How to create Java getters and setters when object key is number. Anything that doesnt look like that is no longer encryption or security its some form of obfuscation.

This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site adventageous, please support us by sharing this posts to your favorite social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title how to store encryption key in java by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.





